Security: #Meltdown and #Spectre , #Kaspersky , #PowerPC
http://www.tuxmachines.org/node/107966
Notices tagged with meltdown, page 3
-
Tux Machines (tuxmachines@mastodon.technology)'s status on Monday, 08-Jan-2018 04:39:59 EST  Tux Machines
Tux Machines
-
Tux Machines (tuxmachines@mastodon.technology)'s status on Sunday, 07-Jan-2018 20:39:51 EST  Tux Machines
Tux Machines
#Meltdown and #Spectre #Linux Perspective
http://www.tuxmachines.org/node/107961 -
lnxw48a1 (lnxw48a1@nu.federati.net)'s status on Sunday, 07-Jan-2018 17:54:51 EST  lnxw48a1
lnxw48a1
@bobjonkman Someone posted this explanation earlier: https://www.raspberrypi.org/blog/why-raspberry-pi-isnt-vulnerable-to-spectre-or-meltdown/
#meltdown #spectre !rpi -
Bob Jonkman (bobjonkman@gs.jonkman.ca)'s status on Sunday, 07-Jan-2018 17:52:28 EST  Bob Jonkman
Bob Jonkman
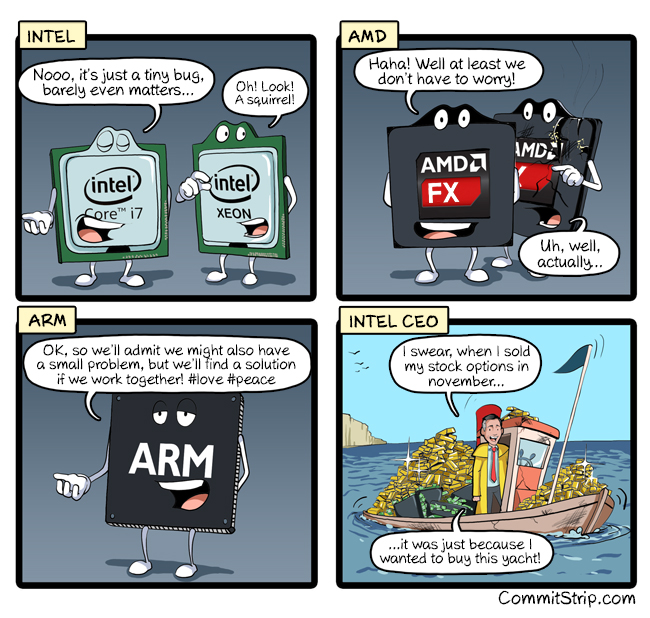
More reactions to #Meltdown and #Spectre: http://www.commitstrip.com/en/2018/01/04/reactions-to-meltdown-and-spectre-exploits/ https://gs.jonkman.ca/attachment/41035 In conversation from web permalink Attachments
-
zigg 💻 (zigg@cybre.space)'s status on Sunday, 07-Jan-2018 10:56:29 EST  zigg 💻
zigg 💻
The best thing you as a user can do to protect yourself against #meltdown and #spectre is install an ad blocker. uBlock Origin, specifically.
Practice good security hygiene, and you’ll have less to worry about when the next threat comes along.
In conversation from cybre.space permalink -
Yes, I Know IT ! 🎓 (yesiknowit@mastodon.social)'s status on Sunday, 07-Jan-2018 08:59:49 EST  Yes, I Know IT ! 🎓
Yes, I Know IT ! 🎓
I don't' really like the title, but the article has some good arguments in favor of open source hardware.
In conversation from mastodon.social permalink -
neville park (nev@social.coop)'s status on Sunday, 07-Jan-2018 07:42:11 EST  neville park
neville park
This post, on why the Raspberry Pi isn't susceptible to #Spectre or #Meltdown, is a wonderfully clear explanation of how they actually work: https://www.raspberrypi.org/blog/why-raspberry-pi-isnt-vulnerable-to-spectre-or-meltdown/ (via @Sangokuss)
In conversation from social.coop permalink Attachments
-
Dr. Roy Schestowitz (罗伊) (schestowitz@gnusocial.de)'s status on Saturday, 06-Jan-2018 23:36:13 EST  Dr. Roy Schestowitz (罗伊)
Dr. Roy Schestowitz (罗伊)
#Meltdown & #Spectre http://blog.dshr.org/2018/01/meltdown-spectre.html In conversation from gnusocial.de permalink Attachments
-
Dr. Roy Schestowitz (罗伊) (schestowitz@gnusocial.de)'s status on Saturday, 06-Jan-2018 11:34:52 EST  Dr. Roy Schestowitz (罗伊)
Dr. Roy Schestowitz (罗伊)
#Meltdown, aka "Dear Intel, you suck" https://marc.info/?l=openbsd-misc&m=151522749523849&w=2 #intel In conversation from gnusocial.de permalink -
Bob Jonkman (bobjonkman@gs.jonkman.ca)'s status on Saturday, 06-Jan-2018 01:25:45 EST  Bob Jonkman
Bob Jonkman
That also gives a good explanation of modern chip architecture: #Pipelining, #Scalar vs. #NonScalar, OutOfOrderProcessing, #SpeculativeExecution. #Spectre #Meltdown #Security In conversation from web permalink -
Dr. Roy Schestowitz (罗伊) (schestowitz@gnusocial.de)'s status on Friday, 05-Jan-2018 20:14:04 EST  Dr. Roy Schestowitz (罗伊)
Dr. Roy Schestowitz (罗伊)
WHY RASPBERRY PI ISN’T VULNERABLE TO #SPECTRE OR #MELTDOWN
https://www.raspberrypi.org/blog/why-raspberry-pi-isnt-vulnerable-to-spectre-or-meltdown/ #raspi #gnu #linuxIn conversation from gnusocial.de permalink Attachments
-
Iwan Setiawan (stwn@quitter.se)'s status on Friday, 05-Jan-2018 20:07:47 EST  Iwan Setiawan
Iwan Setiawan
A collection of #Meltdown/#Spectre postings https://lwn.net/Articles/742999/ In conversation from quitter.se permalink -
Michael Vogel (heluecht@pirati.ca)'s status on Friday, 05-Jan-2018 16:06:16 EST  Michael Vogel
Michael Vogel
XKCD hat sich auch zu #Meltdown und #Spectre geäußert
https://xkcd.com/1938/
http://www.explainxkcd.com/wiki/index.php/1938In conversation from pirati.ca permalink -
jEsuSdA (jesusda@quitter.es)'s status on Friday, 05-Jan-2018 12:29:18 EST  jEsuSdA
jEsuSdA
Aplico el parche de #Meltdown que baja el rendimiento un -30%, pero luego hago limpieza profunda de pelusas de polvo dentro de la caja de la CPU = +30% de rendimiento. Conclusión, me quedo como estaba. ? In conversation from quitter.es permalink -
Iwan Setiawan (stwn@quitter.se)'s status on Friday, 05-Jan-2018 09:38:06 EST  Iwan Setiawan
Iwan Setiawan
A simple explanation of the diffs: #Meltdown vs #Spectre https://danielmiessler.com/blog/simple-explanation-difference-meltdown-spectre/ In conversation from quitter.se permalink Attachments
-
Antanicus (antanicus@social.coop)'s status on Friday, 05-Jan-2018 09:33:15 EST  Antanicus
Antanicus
"To make the best use of the TLB, every mainstream operating system splits the range of virtual addresses into two. One half of the addresses is used for each program; the other half is used for the kernel."
Basically, #Meltdown and #Spectre are exploits of what already is an exploit of the TLB design... Interesting stuff!
https://arstechnica.com/gadgets/2018/01/whats-behind-the-intel-design-flaw-forcing-numerous-patches/
In conversation from social.coop permalink -
úlfur 🐺 (ulfur@mastodon.social)'s status on Friday, 05-Jan-2018 09:25:01 EST  úlfur 🐺
úlfur 🐺
Intel facing class-action lawsuits over Meltdown and Spectre bugs
Plaintiffs claim compensation for security flaws and alleged slowdown that fixing computers will cause, while corporations count cost of corrections
In conversation from mastodon.social permalink -
BjarniBjarniBjarni 🙊 🇮🇸 🍏 (herrabre@mastodon.xyz)'s status on Friday, 05-Jan-2018 09:18:15 EST  BjarniBjarniBjarni 🙊 🇮🇸 🍏
BjarniBjarniBjarni 🙊 🇮🇸 🍏
Prediction:
Software will be used to mitigate #meltdown and #spectre, slowing everything down.
In 2020, a new line of Intel CPUs hit the market where you pay a premium for "virtual security extensions" (VSE) that let you turn off the mitigations.
Google, AWS buy truckloads.
Intel profites.
Yay!
In conversation from mastodon.xyz permalink -
r҉ustic cy͠be̸rpu̵nk🤠🤖 (cypnk@mastodon.social)'s status on Friday, 05-Jan-2018 08:21:27 EST  r҉ustic cy͠be̸rpu̵nk🤠🤖
r҉ustic cy͠be̸rpu̵nk🤠🤖
Just FYI, the #OpenBSD project knew about the potential harm of #Spectre and #Meltdown 11 years ago
https://marc.info/?l=openbsd-misc&m=118296441702631&w=2
This is before exploits routinely started getting catchy names and even before MySpace was a thing. Let alone Twitter and Facebook was around to share news of the impending CPU apocalypse
Too bad so few people listened
https://mastodon.social/media/I10ysFRGxesWg61C5gU
https://mastodon.social/media/-_luWj8UwuEKaeoIq74In conversation from mastodon.social permalink -
Tux Machines (tuxmachines@mastodon.technology)'s status on Friday, 05-Jan-2018 08:04:48 EST  Tux Machines
Tux Machines
#Hardware #Security Fiasco: The Latest
http://www.tuxmachines.org/node/107901 #Meltdown #SpectreIn conversation from mastodon.technology permalink