Show Navigation
Conversation
Notices
-
With key based identity it wouldn't be too difficult to rule out impersonation cases, I shouldn't think.
-
Key-based identity is probably the most intrusive change to the codebase I plan to introduce. When I do introduce it is probably going to be when postActiv diverges enough from the GNU social codebase we won't easily be able to import changes in upstream (not that this is probably a concern anyways, it kind of uh, seems pretty abandoned now)
-
@maiyannah You mean like with public key signatures? Yeah, it would make that pretty hard. Even a system where all the private key stuff happens on server would at least limit the ability to impersonate to just the people with admin level access.
 Annah
Annah
 Annah
Annah
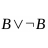 Verius
Verius
